Home » Zero Trust Security: A New Model for Cybersecurity

In today’s digital world, where data breaches and cyberattacks are getting increasingly sophisticated, conventional network security models are proving insufficient. A new approach, known as “Zero Trust,” is gaining popularity as a more robust and effective means to protect sensitive information.
Zero Trust is a security model that assumes that any device, user, or application accessing a network is potentially hostile unless proven otherwise. Unlike traditional perimeter-based security, which focuses on defending a network’s boundaries, Zero Trust requires constant verification and authentication of every request, regardless of its source.
Cybersecurity Awareness Training is Essential in India
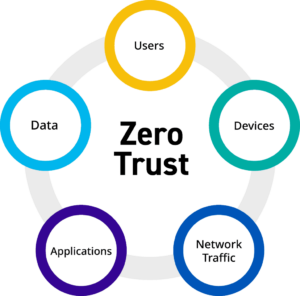
The conventional network security approach, which relies heavily on firewalls and intrusion detection systems, is vulnerable to attacks that bypass the perimeter. Zero Trust addresses these limitations through:
Implementing Zero Trust demands a comprehensive approach that involves multiple key components:
While Zero Trust offers significant advantages, its implementation can be quite difficult. Organizations may need to invest in new technologies and processes, and which may face opposition from employees who are used to traditional security models. Additionally, Zero Trust demands a cultural shift towards a more security-conscious mindset.
Tackle Cyber Bullying? A Comprehensive Look at Legal Remedies
Conclusion
As the threat landscape constantly evolves, Zero Trust is emerging as a crucial component of modern network security. By shifting the focus from perimeter protecting to verifying every access request, Zero Trust can help organizations better safeguard their sensitive data and reduce the risk of cyberattacks.
Lingaya’s Vidyapeeth stands out as the ideal choice for pursuing a BTech CSE in cybersecurity. Being the best university in Delhi NCR and with its expert faculty, cutting-edge curriculum and modern infrastructure, students receive top education that equips them with practical skills and theoretical knowledge vital for succeeding in the cybersecurity field. So, what are you waiting for? Apply now!
From
Manisha Vashisht
Asst. Professor in CSE Dept.
Lingaya’s Vidyapeeth
Best CSE Colleges in Faridabad
August 24, 2024
RECENT POSTS
CATEGORIES
TAGS
Agriculture Agriculture future AI Architecture artificial intelligence BA English BA Psychology BTech Engineering Business management career Career-Specific Education career guide Career Opportunities career option career scope Civil engineering commerce and management Computer Science Computer science engineering Data science degree education Engineering engineering college Engineering students English Literature english program Exam tips Fashion Design Fashion design course Higher Education Journalism journalism and mass communication law Law career Machine Learning MA Psychology Master degree mathematics MBA Mechanical Engineering Pharmacy Psychology Research and Development students
University Address: Nachauli, Jasana Road, Faridabad, Haryana
Toll Free: 1800-120-4613
Mobile : 8447744303 | 8447744304 | 8447744306 | 8447744309
Address: C-72, Second Floor, Shivalik, Near Malviya Nagar,
Above HDFC Bank, New Delhi 110017
Ph.No. - 011-46570515 / 45138169 / 41755703 / +91-7303152412
Jagmani Kutir, Ground Floor, Road No-1, Rajeev Nagar,
Near Darbar Marriage Hall, Patna-800024, Bihar
Contact No: 9818352069/8130120095
Mail: [email protected]
Copyrights © 1998 - 2025 Lingaya's Vidyapeeth (Deemed To Be University). All rights reserved.
It is important to note that the following email IDs and domains are fraudulent and do not belong to our university.
LV only conducts physical/online verification of any document related to examination on the following email id: